PairLoSh - Privacy Preserving Crowdsensing Mechanism
Introduction
In today’s digital landscape, ensuring the security and privacy of data shared among people and applications is a critical concern for me and many others in the field. Data loss, theft, or corruption risks are substantial and pose significant challenges for everyone involved. This has led to a growing focus on privacy-preserving technologies, which aim to protect shared data from unauthorized access and maintain individual privacy.
These technologies are crucial, offering several benefits, including protecting sensitive information, maintaining data utility, compliance with stringent regulations, and building trust among users. One area where these methods have become particularly relevant is mobile crowdsensing, which introduces unique challenges, such as motivating users to contribute their data willingly.
To combat these challenges, reverse-auction mechanisms have incentivized data sharing. Yet, this approach has issues, as the bidding process can reveal sensitive personal information. While differential privacy techniques have been proposed to secure bids and protect user privacy, their effectiveness heavily depends on the trust placed in the data processing platform. In situations where this trust is lacking, the data remains vulnerable.
Moreover, in mobile crowdsensing, preserving the privacy of user locations is a significant concern. Companies value location data for various purposes, from managing traffic to providing navigational aids, yet achieving privacy without sacrificing location accuracy proves to be a complex issue.
To address these challenges, I propose an innovative solution that introduces a single-agent model to establish a trust boundary between the User and all other parties. This approach can be designed to work with any data, but further research is necessary to verify its effectiveness.
The single-agent model is proposed to simplify trust management by reducing the number of parties directly handling sensitive data, aiming to increase overall system security.
Understanding the Framework and Technologies Behind Our Privacy-Preserving Solution
Mobile Crowdsensing: The Power of Collective Data Gathering
Mobile crowdsensing leverages the widespread availability of mobile devices, making it a potent tool for data collection across many participants.
Mobile crowdsensing harnesses the capabilities of mobile devices to gather and analyze data from a vast number of participants. This approach leverages crowdsourcing, where tasks or data collection are distributed among numerous individuals, typically via an online platform or mobile application. This method allows for extensive data collection at a granular level, making it invaluable for various applications, from urban planning to environmental monitoring.
Defining Trust Boundaries: Essential for Data Security
A Trust Boundary defines the limits of trust between entities, including applications or users that might not be fully trusted. Establishing a lower trust boundary is crucial as it helps minimize the risk of security breaches and unauthorized access to sensitive data or resources. This is particularly important in environments where data security and user privacy are paramount.
Privacy-preserving Incentive Mechanism (PPIM): Safeguarding User Data
PPIM uses techniques like anonymization and data minimization to enhance privacy, which are critical for maintaining the confidentiality and integrity of user data.
A Privacy-preserving Incentive Mechanism (PPIM) is essential in systems where incentives are used to encourage user participation. PPIM employs various techniques such as anonymization, minimization, and aggregation to ensure user data remains secure throughout the incentive process. This mechanism is critical in maintaining the confidentiality and integrity of user data while still encouraging active participation.
Distributed Location Privacy Preserving Mechanism (DLPPM): Protecting Location Data
The Distributed Location Privacy Preserving Mechanism (DLPPM) utilizes techniques and protocols to protect users’ location privacy in distributed networks. By allowing users to share their location information anonymously and in a controlled manner, DLPPM addresses significant privacy concerns using strategies like data encryption, aggregation, and obfuscation to ensure location data remains private and secure.
Location Privacy Using Gaussian Distribution: A Mathematical Approach
Employing the Gaussian distribution, commonly known as the standard or bell-shaped curve, adds privacy to location sharing. This probability distribution is characterized by its symmetry around the mean, decreasing probability as values deviate from the center. Applying this method to location data provides a privacy-preserving layer that helps obscure users’ precise locations, enhancing privacy while maintaining utility.
Applying Gaussian distribution for location privacy is complex and must be calibrated carefully to balance privacy with data utility.
Exploring Advances and Challenges in Privacy-Preserving Mobile Crowdsensing
Significant research has been conducted on mobile crowdsensing (MCS) to enhance privacy and optimize data collection methods. Various scholars have contributed to understanding and solving the intrinsic privacy challenges associated with MCS, mainly when sensitive data like location or personal bids are involved.
Time-Window Dependent Privacy in Crowdsensing
Xu et al. delved into the challenges associated with time-window-dependent bids in mobile crowdsensing, which previously lacked robust privacy solutions. Their research introduced two novel techniques: the Mechanism for Single Time Window (MST) and the Mechanism for Multiple Time Window (MMT), each designed to safeguard user data within designated time frames.
Spectrum Sensing and User Incentives
Jin et al. focused on crowdsourced spectrum sensing, a technique that improves access to wireless networks through user participation. They critiqued the privacy inadequacies of current reverse-auction-based incentive mechanisms and proposed PriCSS, an alternative designed to minimize privacy loss. This demonstrates the ongoing need for improved privacy-preserving frameworks in MCS.
Bid Privacy and Agent-Based Obfuscation
Both Xu et al. and Jin et al. highlighted the privacy risks inherent in user bids, setting the stage for Wang et al.’s subsequent efforts. Wang et al. proposed a sophisticated privacy-preserving mechanism that employs multiple agents to obscure users’ accurate bids from an honest-but-curious platform. However, this approach introduced additional trust boundaries involving these agents.
Dynamic Pricing Policies in MCS
Liu et al. explored adaptive privacy-preserving mechanisms in MCS, particularly under dynamic conditions. Using reinforcement learning, they developed a method allowing platforms to adjust pricing policies dynamically in response to participants’ changing privacy needs, building on the foundation of privacy-preserving incentive mechanisms.
Addressing Location Privacy in Location-Based Services
Dua, Singh, and Bapat discussed the implications of continuous location tracking in location-based services (LBSs), highlighting the generation of sensitive information and the risks involved. Their work expands on the various approaches to preserving location privacy, emphasizing the necessity of robust mechanisms in this context.
Survey of Privacy Preservation Techniques
Kim, Edemacu, and Jang provided a comprehensive survey of the current state of privacy preservation in location-based mobile crowdsensing. Their review detailed three distinct models of privacy management: Mobile Crowdsensing with a Trusted Party (MCS-TP), which involves a server, workers, and a trusted third party; MCS-LOC, focused on location-based data where the worker handles privatization; and MCS-P2P, which facilitates peer-to-peer data privatization among workers before data is sent to the Server.
These studies underscore the complex and evolving nature of privacy challenges in mobile crowdsensing and the continuous innovation required to address these concerns effectively.
Problem in Existing Systems
In my review of the current landscape in mobile crowdsensing and privacy preservation, I’ve identified two primary issues that frequently emerge across different systems: the placement of the trust boundary and the associated implementation costs. Most secure systems advocate for a direct trust boundary between an individual user (worker) and all other parties to effectively minimize the risk posed by potentially malicious actors. However, achieving this ideal setup often comes with substantial challenges.
A significant concern stems from the implementation strategies suggested by Wang et al., which involve deploying a new agent for each User. While potentially enhancing privacy, this method leads to considerable implementation expenses due to the need for multiple agents, each requiring maintenance and coordination.
Consider the high costs and potential complexity when deploying new agents for each user as suggested by Wang et al., as it may lead to substantial implementation expenses.
Design Goals for PairLoSh
To address these issues, I propose a new mechanism, PairLoSh, designed to establish a user-centric trust boundary while allowing users to share their obfuscated location data with a server securely. Several vital objectives guide the development of PairLoSh:
- Privacy Preservation: The foremost priority of PairLoSh is to ensure users’ location data privacy. The mechanism is designed to prevent adversaries, including other users, honest-but-curious servers, and external threats, from determining any individual’s precise location.
- Scalability: PairLoSh must support a large user base, which is typical in crowdsensing applications. The system must efficiently handle numerous data-sharing requests and manage user pairing allocations seamlessly across many users.
- Minimal Encrypted Communication: Enhancing privacy and security further, PairLoSh limits the need for extensive communication between the Server and other system components. It reduces the frequency of interactions between the Agent and the Server, ensuring that any necessary communications, especially those involving direct user interaction, are encrypted.
- Trust Boundary Definition: PairLoSh explicitly places the trust boundary between each individual User and all other elements within the system. This strategic placement reduces dependence on the trustworthiness of external systems or agents, thus bolstering the mechanism’s overall security.
- Minimal User Interaction: To ensure accessibility and ease of use, especially for devices with limited computational resources, PairLoSh is designed to minimize the need for user interactions when sharing location data with the Server.
PairLoSh is designed with key objectives such as scalability and minimal user interaction to address current shortcomings in mobile crowdsensing systems efficiently.
Through these design goals, PairLoSh aims to resolve the prevalent issues in existing systems while setting a new standard for privacy and efficiency in mobile crowdsensing.
Implementing PairLoSh for Enhanced Location Privacy
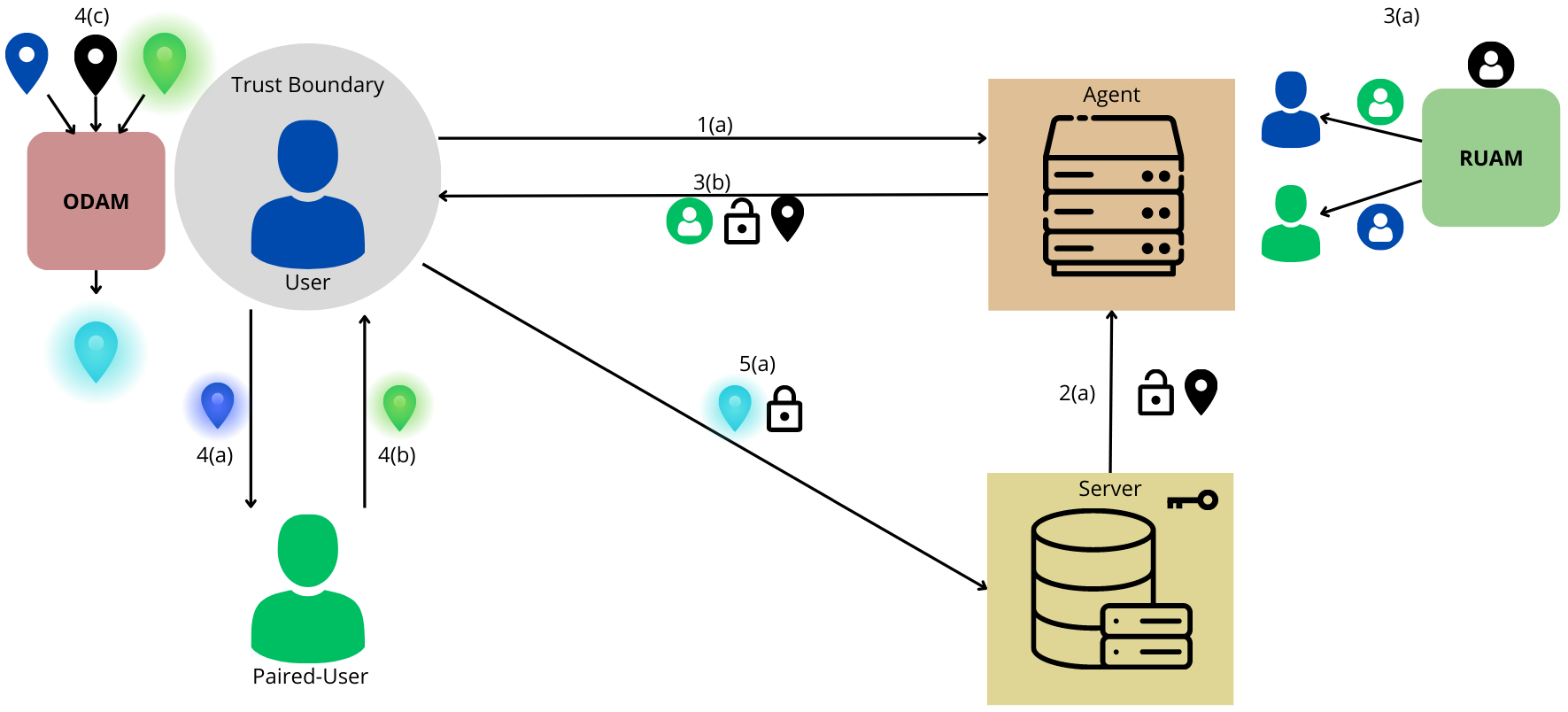
The PairLoSh architecture aims to robustly secure user location data through a series of systematic and encrypted interactions, ensuring maximum privacy preservation.
In developing PairLoSh, I aimed to create a system that effectively obfuscates a user’s location before sharing it with the Server. This methodology incorporates several vital processes: pairing, obfuscation, aggregation, encryption, and secure sharing. Each component plays a crucial role in ensuring the privacy and security of the data transmitted within the system.
PairLoSh Architecture Overview
The architecture of PairLoSh, as illustrated in the figure below, details all interactions within the mechanism for a single user. This process is replicated for each User within the system, ensuring consistent privacy protection across all data points.
Detailed Breakdown of PairLoSh
This system is structured around two main modules: the Obfuscated Data Aggregation Module (ODAM) on the user side and the Randomized User Allocation Module (RUAM) on the agent side. Each module has specific functions critical to the privacy-preserving process:
- ODAM (Obfuscated Data Aggregation Module): Situated on the user side, ODAM is responsible for the initial processing of location data. This includes the obfuscation steps, where the actual location data is altered to prevent exact location pinpointing while still being useful for the intended application.
- RUAM (Randomized User Allocation Module): Positioned on the agent side, RUAM handles users’ dynamic allocation and pairing. This module ensures that the obfuscated data from different users can be aggregated to enhance privacy before being sent to the Server.
Role of the Agent and Server
The Agent is pivotal in managing data-sharing requests and allocating and assigning user pairings based on the system’s needs. The Agent and Server interaction is deliberately limited to essential communications to minimize potential security risks. The Server, for its part, primarily interacts with the Agent to exchange necessary public keys and to receive aggregated location data.
Secure Communication
To ensure that the privacy of the User’s location data is maintained throughout the process, all interactions between the User and the Server involving the obfuscated location data are encrypted using the Server’s public key. This step is crucial for protecting the data from potential interception or unauthorized access during transmission.
Through these meticulous steps, PairLoSh addresses critical privacy concerns in mobile crowdsensing by providing a robust framework that secures user data against various threats. The methodology ensures that each User’s location data is protected through multiple layers of security, making it a reliable and effective system for privacy-preserving mobile crowdsensing.
The Intricacies of PairLoSh Interactions
In the PairLoSh system, the dynamics of data exchange and privacy preservation are meticulously organized through several fundamental interactions:
- User-Agent Interaction: As a user, I notify the Agent of my intention to share location data with the Server. This is the initial step that triggers the subsequent privacy-preserving processes.
- Server-Agent Communication: The Server then sends its public key and an advertised location to the Agent. This setup not only secures the locations received from me by ensuring they are encrypted but also assists in estimating my perturbed location. It enables the Agent to select user-pairings within a particular geographic area strategically.
- Agent-User Coordination: Utilizing the Random User Allocation Module, the Agent assigns me a user pairing. The agent communicates this pairing back to me without revealing it to the Server, maintaining confidentiality. The agent also sent me the necessary public key and location details for the next steps.
- User-Paired User Exchange: I then obfuscate my location using a Gaussian distribution method, connect with my paired User, and exchange our obfuscated locations. Subsequently, I use the Obfuscated Data Aggregation Module to synthesize a shared obfuscated location from this data.
- User-Server Transmission: Finally, I encrypt the shared obfuscated location using the public key provided earlier and send it to the Server.
Upon receiving this data, the Server decrypts it using its private key to obtain my shared obfuscated location. This location is not only disguised through the Gaussian distribution but also strategically shifted according to the randomly determined user pairing. I can set the degree of this shift unless the Server specifies otherwise.
Understanding the Obfuscated Data Aggregation Module (ODAM)
The Obfuscated Data Aggregation Module (ODAM) is a critical component on my system side. It processes the obfuscated location data to generate a shared obfuscated location, ensuring that the precise details of my actual whereabouts remain protected. The following figure illustrates the primary functions and workflow of ODAM.
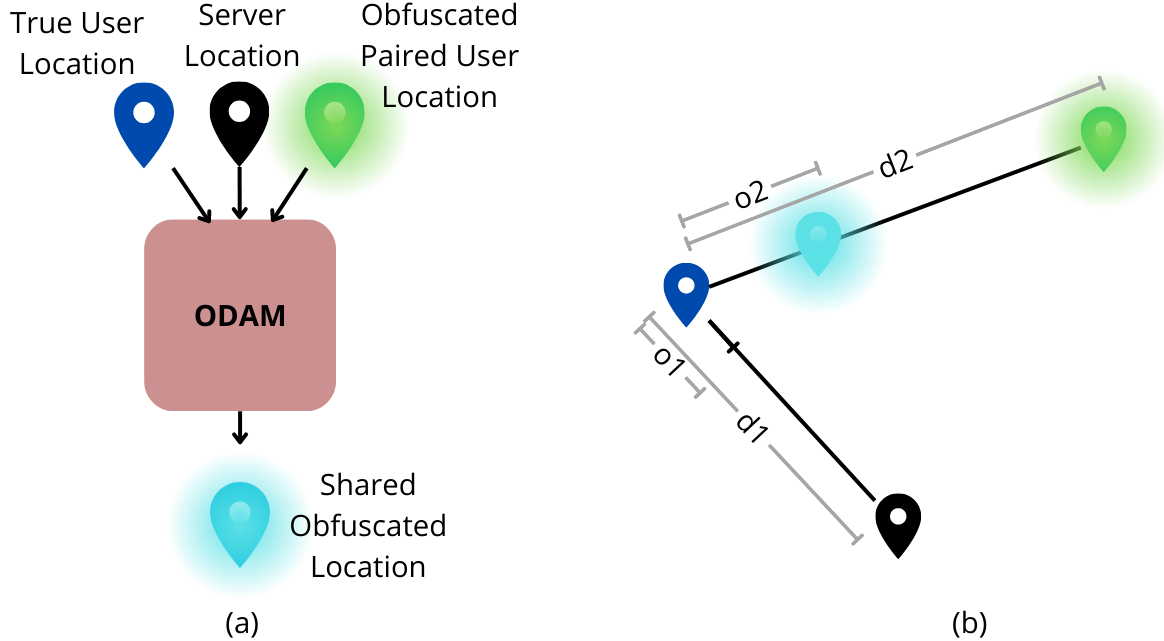 Obfuscated Data Aggregation Module
Obfuscated Data Aggregation Module
In ODAM, I input my actual location, the server-provided location, and the obfuscated location from my paired User. The module then computes a shared obfuscated location by employing a mathematical formula to balance the distances and desired obfuscation level:
\(\frac{o_{1}}{d_{1}} = \frac{o_{2}}{d_{2}}\) \(\frac{o_{1}}{d_{1}} * d_{2} = o_{2}\)
Here, $o_{1}$ represents a customizable value that I can adjust to increase or decrease the accuracy of the shared location, ranging from 1% to 50% of the distance $d_{1}$. The module then obfuscates my location by $o_{2}$, producing the shared obfuscated location.
The User’s location is then obfuscated by $o_{2}$ to generate the shared obfuscated location of the User.
Delving into the Randomized User Allocation Module (RUAM)
The Randomized User Allocation Module (RUAM), managed by the Agent, plays a pivotal role in assigning user pairings. This module is designed to enhance privacy by randomly pairing users who have expressed a desire to share their location data.
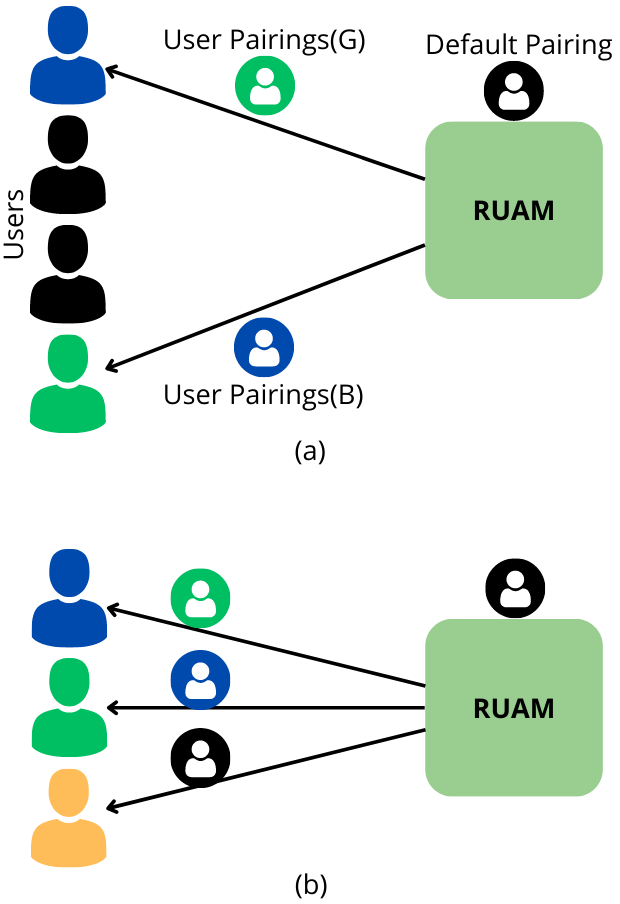 Randomized User Allocation Module
Randomized User Allocation Module
RUAM operates by randomly selecting two users from those who have advertised their intent to share their location data and pairing them together accordingly. For each User, it generates a user pairing and communicates this information securely. In scenarios where an odd number of users participate, the module pairs the odd User with a default location set during initialization, ensuring no user is left unpaired.
These structured interactions and modules within PairLoSh collectively ensure robust privacy protection while facilitating practical location sharing in mobile crowdsensing environments.
Analysis: Trust Boundaries and Resilience Against Bad Actors in PairLoSh
One of PairLoSh’s standout features, which I consider a significant strength, is the strategic placement of the trust boundary. Unlike other systems, where the trust boundary might lie between pairs in peer-to-peer communication or between an agent and the Server, PairLoSh establishes the trust boundary directly between the individual User and all other components. This setup is particularly advantageous as it minimizes reliance on the trustworthiness of different systems and enhances overall security, significantly if part of the system is compromised or a lousy actor is involved.
Identifying and Mitigating Risks from Bad Actors
In the PairLoSh system, three potential types of bad actors could threaten the mechanism’s integrity:
- The Malicious Worker: This is the most obvious threat, where a worker could potentially feed false information to their paired worker and subsequently to the Server. However, due to the design of PairLoSh, such a worker cannot ascertain the exact location of another honest worker they are paired with. Moreover, unless there is a coordinated attack involving a network of bots, the impact of false data from a single bad actor is minimal, especially with a large sample size, ensuring robustness.
- The Pairing Agent: A malicious pairing agent could pair users strategically to introduce noise or bias into the system. Nevertheless, this risk is mitigated by users not sharing their exact locations with the Agent, reducing the potential for targeted manipulation.
- The Honest-but-Curious Server: Even a server that does not intend to misuse data but is curious could pose a risk. However, in PairLoSh, the Server receives only obfuscated data from multiple sources, preventing it from extracting personal information about individual workers. Thus, workers’ privacy remains intact under this system.
Potential Server Tactics and System Robustness
A possible tactic by the Server to breach privacy could involve repeatedly querying for noisy location data to pinpoint a user’s exact location over time, exploiting the Gaussian distribution. However, PairLoSh counters this by randomizing pairings for each data request, ensuring that the aggregated data varies each time and does not converge on a specific point, thereby maintaining location privacy.
Versatility and Adaptability of the System
While I chose to focus on location-based data for its simplicity and straightforward calculations, the underlying principles of PairLoSh are not confined to just this type of data. The Obfuscated Data Aggregation Module (ODAM) can be adapted to work with various types of data. Any new scheme would simply need to aggregate data in a way that is still meaningful to the Server but does not introduce excessive noise, thereby maintaining the reliability and utility of the data.
Through this analysis, it is clear that PairLoSh addresses fundamental privacy concerns and demonstrates a resilient structure capable of adapting to different data types and resisting potential threats from various bad actors.
Evaluation and Future Work: Assessing PairLoSh and Charting the Path Forward
Understanding PairLoSh’s performance through key metrics like privacy leakage and accuracy-to-distance ratio will be crucial in its real-world applicability and refinement.
Performance Evaluation
Due to time constraints, PairLoSh has yet to undergo a formal evaluation to assess its performance and real-world applicability. However, understanding how well this system works is crucial for future development. To effectively measure the performance of PairLoSh, I plan to employ several key metrics:
- Privacy Leakage: This metric will help determine how much a user’s location data is disclosed within the mechanism, encompassing potential exposure to paired users, other system users, the Agent, the Server, and any external parties.
- Accuracy to Distance Ratio: This will assess the accuracy of the perturbed location relative to the distance between the User and their paired User, helping understand the effectiveness of the obfuscation technique.
- Deviation from True Location: This measures how much the User’s perturbed location deviates from their actual location, providing insights into the system’s privacy-preserving efficacy.
To evaluate these aspects, I intend to conduct a location-sharing crowdsensing experiment using real-world GPS datasets, such as mobility traces of taxi cabs or student population movements within specific campus areas. This practical application will allow me to gather empirical data and refine the system based on its performance in real-world scenarios.
Future Work
Looking ahead, there are several avenues for further development and enhancement of PairLoSh:
- Practical Implementation and Deployment: The next logical step is the practical implementation and deployment of PairLoSh. Testing the system in real-world environments will provide invaluable insights and help identify areas for improvement.
- Incorporating Incentive Mechanisms: Integrating an incentive system, possibly inspired by Wang et al.’s bid system, could encourage more widespread adoption and active participation in sharing location data, enhancing the overall utility of the crowdsensing ecosystem.
- Adapting Modules for Various Data Types: While PairLoSh currently focuses on location data, the underlying modules could be modified to handle different data types. This adaptability would expand PairLoSh’s applicability to various domains beyond location-based services.
- Reducing System Complexity: Further work could aim to simplify PairLoSh’s overall complexity, making it more accessible and computationally inexpensive for remote crowdsensing participants. Streamlining the system could lead to broader adoption and fewer barriers for users with limited technical resources.
Conclusion
In this blog post, I have introduced PairLoSh, a novel mechanism designed to share location data with a server while safeguarding the User’s actual location. PairLoSh strategically employs two key modules: the user-sided Obfuscated Data Aggregation Module (ODAM) and the agent-sided Randomized User Allocation Module (RUAM). This innovative approach builds upon prior research in mobile crowdsensing. It integrates and enhances existing location privacy solutions, such as employing Gaussian distribution techniques, while strictly maintaining the trust boundary at the individual user level.
Throughout my discussion, I have analyzed PairLoSh’s robustness, particularly in the context of potential threats posed by bad actors within the system. This analysis underscores the importance of designing privacy-preserving mechanisms that are resilient to potential security breaches.
Looking ahead, I have outlined a series of performance evaluation metrics that could be employed to assess the effectiveness of PairLoSh, including privacy leakage, accuracy-to-distance ratio, and deviation from the proper location. These metrics will be crucial in a forthcoming empirical study to validate and refine the mechanism using real-world data scenarios.
By developing and enhancing PairLoSh, I aim to contribute to the broader field of mobile crowdsensing by providing a reliable, efficient, and secure method for location data sharing. This mechanism promises to enhance user privacy and paves the way for future research and development in privacy-preserving technologies.
Acknowledgement
This project was a joint effort with my skilled colleague, Dominic Adams. Together, we developed PairLoSh as part of our assignment for the CSEC-759 Advanced topics in Network and Distributed System Security course at RIT.
You can access the project by clicking here.
References
- Dua et al. - Location Privacy-Preserving Mechanism - A Data-Driven Approach
- Xiaocong Jin and Yanchao Zhang - Privacy-Preserving Crowdsourced Spectrum Sensing
- Kim et al. - Privacy-preserving mechanisms for location privacy in mobile crowdsensing: A survey
- Liu et al. - An Incentive Mechanism for Privacy-Preserving Crowdsensing via Deep Reinforcement Learning
- Kato Mivule - Utilizing Noise Addition for Data Privacy, an Overview
- Wang et al. - Towards Privacy-preserving Incentive for Mobile Crowdsensing Under An Untrusted Platform
- Xu et al. - Incentive Mechanisms for Time Window Dependent Tasks in Mobile Crowdsensing